ALERT! – QR Fraud, Microsoft 365 App Phishing – ALERT!
It seems that hackers just don’t give up trying to hurt you. They are using every possible avenue to attack you, your device and your information.
QR Fraud Alert
Everyone by now has seen those QR speckled squares just about everywhere. After the pandemic took hold they showed at restaurant tables where you scan one to bring up the menu. They are used to open websites, download apps, collect loyalty program points, make payments and transfer money, and give to charity. We have here a practical technology that has become nearly indispensable. But, predictably, cyber criminals have launched a variety of QR-based schemes. Using those speckled squares can go sideways fairly quickly. We’ll show you how and how to use them without fear.
So whats happening with the QR Code? First of all you have no idea what you are scanning. Its just not readable by human eyes. So we rely on the honesty of the code creator. That never works online. A QR code created by cyber criminals might point to a phishing site that looks like the login page of a social network or online bank. A QR code can trick users into downloading malware instead of the intended game or tool. At that point, the sky’s the limit; malware can steal passwords, send malicious messages to your contacts, and more. What else can the QR code do? It may contain a command to perform all kinds of actions including;
- Add a contact;
- Make an outgoing call;
- Draft an e-mail and populate the recipient and subject lines;
- Send a text;
- Share your location with an app;
- Create a social media account;
- Schedule a calendar event;
- Add a preferred Wi-Fi network with credentials for automatic connection.
How do you protect yourself? Good question. Follow these simple rules to protect yourself when using QR codes;
- Do not scan QR codes from obviously suspicious sources;
- Pay attention to the links displayed when scanning the code. Be especially wary if the URL has been shortened, because with QR codes, there is no compelling reason to shorten any link. Instead, use a search engine or official store to find what you’re looking for;
- Do a quick physical check before scanning a QR code on a poster or sign to make sure the code isn’t pasted over the original image;
- Use a program such as Kaspersky’s QR Scanner (available for Android and iOS) that checks QR codes for malicious content.
QR codes can also hold valuable information such as e-ticket numbers, so you should never post documents with QR codes on social media.
Microsoft Office 365 Apps
So who is not using Microsoft Office?
So since everybody, and I mean everybody, is using Microsoft Office we know why this phishing attack is happening. Phishers are targeting Microsoft Office 365 users more frequently. The hacker are so clever they are sending specialized links that take users to their organization’s own email login page. After logging in the link prompts them to install a malicious but innocently named app. Once installed the app gives the attacker persistent, password-free access to any of the user’s emails and files. These are then plundered and used to launch malware and phishing scams against others.
Use caution. The app may look like this.
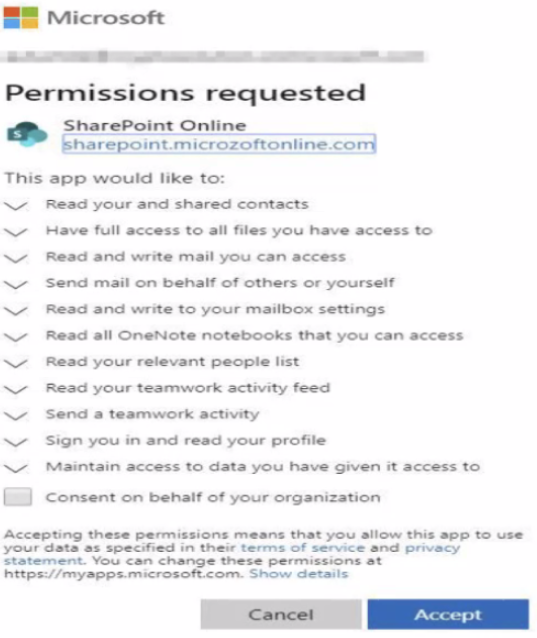
The malware is fairly well thought out and allows attackers to even bypass multi-factor authentication. This happens because they have been approved by the user after logging in. The attack is so well thought out that the malware will persist in a user’s Office 365 account indefinitely until removed and can survive even a password reset.
Proofpoint published some new data on the rise of these malicious Office 365 apps, noting that a high percentage of Office users will fall for this scheme. “High percentage” means that you are likely to fall for it! Last year Proofpoint reported on a service in the cyber criminal underground where customers could access various Office 365 accounts without a username or password. The service also advertised the ability to extract and filter emails and files based on selected keywords, as well as attach malicious macros to all documents in a user’s Microsoft OneDrive. Told you it was well thought out.
How has Microsoft responded? The world’s largest software maker added a policy that allows Office 365 administrators to block users from consenting to an application from a non-verified publisher. Also, applications published after November 8, 2020, are coupled with a consent screen warning in case the publisher is not verified, and the tenant policy allows the consent. Microsoft’s instructions for detecting and removing illicit consent grants in Office 365 are here.
So the bottom line here the same old cyber security point I stress repeatedly. Be careful what you click on. I don’t care if does say Microsoft. Think twice about any app that wants to introduce itself to you. Alert your IT department if you do suspect this type of attack or other malware.






