WannaCry Ransomware – So Whats Happening?
WannaCry notice
A worldwide ransomware attack launched this past weekend hit computers in over 150 countries. The United States was less affected than other countries. Security experts estimated that the cyber attack crippled 200,000 computers in more than 150 countries. But that number could be low. Scarce reports have Russia and China as being especially hard hit by the malware.
The global attack was carried out by hackers who exploited a flaw in Microsoft’s Windows operating system first discovered by the National Security Agency (NSA). In April of this year the flaw and a hacked NSA cyber tool to exploit it became public when they were posted on the Internet by a hacker group known as Shadow Brokers.
In Great Britain the loss of computing systems prevented doctors from accessing patient files and caused emergency rooms to divert patients. According to Prime Minister Theresa May there is no evidence that patient data had been stolen. British officials stated 48 of Britain’s 248 public health trusts had come under attack. All but six are back to normal.
A spokesman for FedEx said: “Like many other companies, FedEx is experiencing interference with some of our Windows-based systems caused by malware. We are implementing remediation steps as quickly as possible.”
One reason the U.S. seems to have been spared from this global attack may have been the work of a British researcher.
The unknown attackers included a “kill switch” in the form of a URL in the malicious code. Experts believe it was a way to control the malware. The kill switch would shut down the attack when the virus sent an online request to a specific website.
A 22-year-old British researcher whose Twitter handle is @MalwareTechBlog discovered the kill switch’s domain name had not been registered. Thinking quickly he purchased the domain name for about $11.00. According to security experts the researcher shut down the malware before the it could reach the U.S. The cyber hero probably stopped a catastrophic malware attack from taking place on U.S. soil. The researcher has confirmed his involvement in a blog post but has insisted on anonymity.
Matthieu Suiche founder of Comae Technologies a cyber security company located in the United Arab Emirates said, “That kill switch is why the U.S. has not been touched so far. But it’s only temporary. All the attackers would have to do is create a variant of the hack with a different domain name.” These variants have sense been discovered on the Internet.
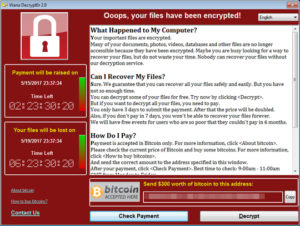
The hackers who launched the attack asked for $300US or $600 in bitcoins to unlock computers but experts advise not paying the hackers. According to security experts victims are left waiting and hoping WannaCry’s hackers will remotely free the hostage computer. The process is done manually over the Internet. That means hackers may have the near impossible task of unlocking thousands of computers one at a time. But the real issues is the payment method, usually in bitcoins. The hackers have no way to know who paid the ransom.
Owners of the locked computer may become desperate and pay the ransom. “But don’t count on getting your files back,”said Matthew Hickey, director of security provider Hacker House.
“The culprits can only restore user’s systems by manually sending the decryption key to each affected computer, which will amount to a time-consuming process,” he said.
“You’re really at the mercy of the human operator. Someone at the other end of the connection,” Hickey said.
Was the malware attack the work of inexperienced cyber criminals or so called script kiddies? Evidence indicates that this could be the case.
First of all the perpetrators included an obvious kill switch in the code but failed to register the domain name. Perhaps they were afraid it could lead back to them.
According to some reports the hackers did manage to rake in about $56,000 in bitcoin payments. But according to Hickey the inefficiency of the payment model may indicate the hackers were not after money at all. “If it was done for money, it wasn’t the smartest way to get it,” he said.
Hickey pointed out that because of the large number of computers infected the asking price could have been much lower and still brought in a nice pay off.
But these hackers do not appear to be experienced or ambitious cyber criminals. They demanded a large ransom and used, at best, a sloppy payment method leaving victims wondering if they were paying for nothing.
According to Hickey, “It removes the incentive to send any money to the attacker.”
But some experts see the fingerprints of North Korea on the malware attack. A New York Times report revealed that intelligence officials and private security experts have found digital evidence pointing to North Korean connected hackers.
The evidence is not definitive but security experts at Symantec believe they have found the same tools used in previous hacks of Sony Pictures Entertainment, the Bangladesh central bank last year and Polish banks in February in the WannaCry malware attack.
Regardless of who carried out the attack make no mistake WannaCry did indeed work and encrypted any machine unlucky enough to encounter it. Security experts and cyber sleuths are working to rescue computers already infected.






