Well Fargo and Bank of America customers need to be on the look out. Cyber criminals have you on their hit list.
Separate reports from security researchers reveal phishing campaigns intent on stealing customer’s credentials.
Armorblox security researchers discovered the phishing campaign and reports that it targets a select group of Bank of America customers to ensure that the malicious emails can bypass various security tools in order to reach the intended victim.
Researchers at Abnormal Security are investigating an even bigger phishing campaign aimed at Wells Fargo customers. Cyber criminals are impersonating the bank’s security team sending out fake alerts to victims with an urgent message to update their security key or lose access to their accounts.
Both campaigns usher victims to malicious domains where they are asked to input their credentials. The information goes directly to the fraudsters. There are no reports thus far that the phishing attack is working but Abnormal Security researchers report that Wells Fargo phishing emails may have reached as many as 20,000 inboxes.
Bank of America
In the Bank of America attack, discovered by Armorblox, the scammers sent phishing emails to customers requesting them to update their email addresses. Victims who clicked on a malicious link embedded in the message were sent to a fake BofA website that looks exactly like the actual Bank of America login page. The scammers collected vital information from victims including email addresses, user names and passwords and other sensitive information used in account take over fraud and other financial crimes.
Chris Morales, head of security analytics at security firm Vectra, told the Information Security Media Group. “Financial institutions have always been one of the highest profile targets for cyber attacks. The attack landscape is no better or worse today than it was at the beginning of the year for financial institutions already dealing with targeted attacks.”
Wells Fargo
In the Wells Fargo phishing campaign Abnormal Security found victims had received emails that appear to come Wells Fargo Security. The fraudsters attempt to steal customers’ data, such as usernames, passwords, PINs and account numbers. The email also included an ICS calendar file that is supposed to store scheduling information, according to the report.
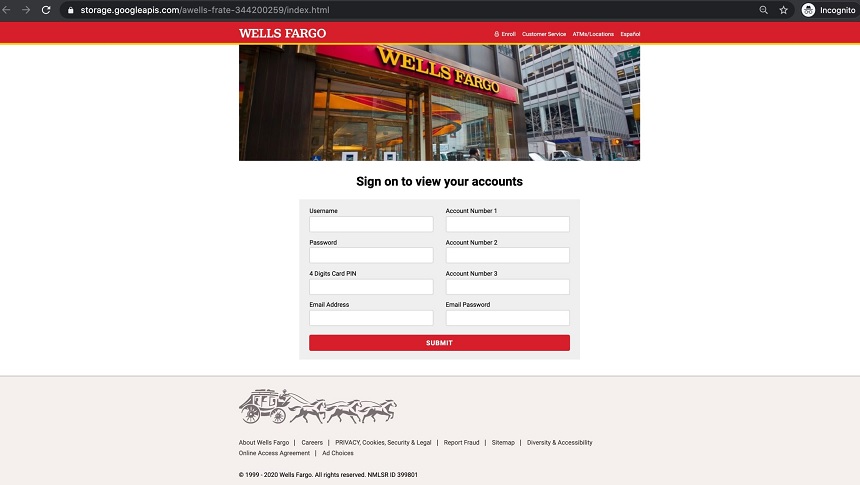
If the victim opens the calendar file they will discover a link to a SharePoint page. This takes the victim to yet another webpage. Finally the victim lands on a page that is malicious and controlled by the fraudsters . Like many other scams this page is a near exact replica of the Wells Fargo website. If customers enter data here it’s collected by the attackers.
According to reports the calendar invite file is designed to encourage victims to click and requests that they open it up on their mobile device.
According to Abnormal Security, “Here, the attacker is attempting to exploit a setting where the event will automatically be added to a user’s calendar. Most of these programs will send an automatic notification to the user and attackers hope that potential victims will click on the event and follow the malicious link. As a result, these attacks are more likely to be seen by recipients.”
